Introduction
The internet of things changes the method data from the actual world is accessed. The infrastructure of smart appliances consists of thousands to millions of small sensor networks with specific computing and networking capabilities to detect the environment. These instruments can provide extremely reliable and resolved information about the sensed phenomenon when they are networked together. There are some problems involved in the process of incorporating.
Security by nature is a technique that assures that protection so much as levels of consumer development and implementation is a critical goal. It highlights the question how safety concerns are always used latter in the development and debugging process in several recent equipment implementations and occasions of IoT layout. Security specifications may finish up getting introduced by recognizing access to production and perhaps other development requirements
In recent decades wireless sensor networks (WSN) have grown from an enticing area of science to a practical technology for different domains (e.g., industrial monitoring in critical infrastructures [1]). Cybersecurity for wireless communications has also progressed, providing significant improvement, such as successful public key authentication method iterations and compact self-healing processes. There is still one specific aspect of the protection of the sensor network that is usually underestimated or ignored: the interaction between the safety specifications the app’s functionality and scope, and the network security. Even so, a given application’s interpretation and specifications have a significant effect on the protection measures that is being used to secure the network. In addition, new WSN standards are being established, however some security challenges seem to be ignored, since these guidelines primarily concentrate on maintaining connectivity among networks. This article is expected for two purposes. Our first aim is to provide an overview of the interaction among conditions, frameworks and authentication methods. We would then specifically describe that how various systems, software and system architectures impact the identification and system integration of safety services. Ultimately, we will provide an outline of the state of the art of sensor cybersecurity methods, figuring out by now security models and key challenges. As for our ultimate convenience, we intend to define the current specifications of the network system and its data encryption. We will also include an overview of these various requirements, concentrating on their protection abilities.
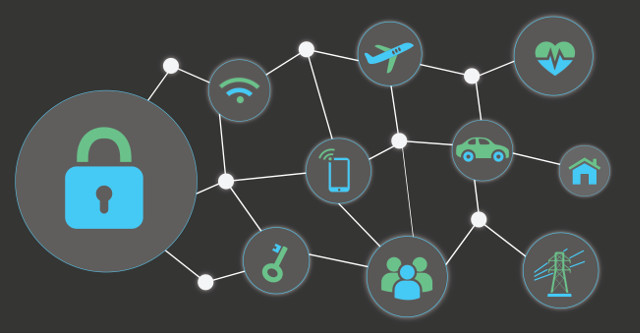
A research performed by Hewlett Packard [3] discovered that there are significant limitations in 70% of all the most widely utilized IoT products. Due to their architecture, IoT applications are responsive to safety risks owing to the unavailability of some of these safety measures such as unreliable networking media inadequate specification of encryption and permission. As a result, everybody, either individual people or businesses, would be affected when IoT is accessible. In particular, the functionalization of domains offers different possibilities for impact and trade. This adds to a number of new possible hazards that should be regarded with respect to data safety and information preservation. See (Fig. 1).
Security concerns and aspects can be remedied by presenting engineers and programmers with sufficient guidance to incorporate safety approaches into IoT applications, thereby enabling consumers to use IoT authentication methods incorporated within the devices [2]. Our reason for carrying out this analysis is because most of the earlier research concentrated exclusively on educational approaches and neglected other kinds of technological and commercial approaches. Even then, in effort to accomplish integrated services as well as all the requirements in those key categories, all three components should function cohesively and simultaneously. The Wireless Sensor and Actuator Network (WSAN) is an application of the Wireless Sensor Network (WSN) and acts as an omnipresent framework with many evolving concepts, including the Internet of Things (IoT), the Industrial IoT (IIoT), the Cyber Physical System (CPS) and the Tactile Internet. To transform the fourth industrial revolution, such technical developments integrate processing, computation, and controlling together with a few with digital networks and communication technology (ICT). The Industry intends to allow established companies smart enough to manufacture large goods with lower prices.
Security Issues, challenges and considerations
In recent days IoT began to acquire significant traction as a result of the growing increase of computer products. Protection, nevertheless, retains one of the significant IoT issues [4] and the primary question posed by various Internet – Of – things investors, and also retains the ability to delay its adoption [5]. It is then deemed a few of the big issues to be tackled in order to encourage IoT in the real world [6]. Security is an essential feature of an IoT system and is connected to
Building security in IoT development
Since we look at 21.4 million smart speakers in operation in 2020, this is a significant concern. The trend is only about to continue as at least 20 percent of Internet searching occurred using google assistant and 22 percent of US individuals have rendered a transaction utilizing the connected Digital app. Since then, IoT system developers often passed on protection to bring goods to consumers quicker. Yet security is a rising issue nowadays and consumers are highly worried regarding the
Organizing IoT devices’ protection development cycle
A comprehensive yet deep cyber protection approach becomes crucial to maintaining the development process of safety devices throughout the computer and network continuum to reduce the threat layer yet which has frequently ignored. Security is never another operation, instead an emerging feature including its IoT environment which would help the development cycle of IoT applications in:
Using fresh appliances and reclamation those around,
Executing innovative products in the network,
Performing
Discussion
Method involves of identification, passwords, and symbols is important for all such operations. Although sensor networks disclose the hidden information during the modification of network management in the development phase confidentiality is threatened. In regard to either the damaging photographs and recordings which are currently shown on smartphones and many certain modern apps such problem is found. Because life-cycle confidentiality contra versions are mainly related to the data obtained,
Conclusion
The IoT is an innovative application that had already achieved substantial strides in software optimization. Within industry, professional fields, as well as for the users themselves, IoT has enormous advantages. Including some realistic methods of doing so, people have focused at the considerations how IoT system protection will be enforced. Companies are now navigating a delicate balance among improving stable IoT while rapidly moving IoT-based products throughout the industry.